Mobile advertising, including user acquisition and retargeting, is a multi-billion dollar industry. And like most high-value industries, it attracts not only legitimate app marketers but also criminals. With the rise of mobile advertising, ad fraud has become a bigger and bigger problem too. In 2018, fraudsters managed to steal 7.6 billion dollars in total from advertisers. And the latest predictions say that this number might have increased to more than 12 billion dollars in 2019.
In this article, you will learn about the most common types of fraud, how to detect them, and what you can do to protect your campaigns against fraud.
WHAT IS MOBILE AD FRAUD?
Mobile ad fraud is a collective term for activities by criminals that aim to steal the marketing budgets of advertisers without delivering any valuable traffic in return. To do so, they use sophisticated technologies to manipulate the media buying process.
HOW MOBILE AD FRAUD WORKS
Fraudsters have developed multiple ways that aim at different stages of the Mobile Marketing Funnel: the impression stage, the click stage or the install stage. While some of them require human manpower on the fraudsters’ side, most are based on technology and more or less automated. Fraudsters even create apps that serve a purpose for the user but contain malicious software that was designed for committing ad fraud.
Learn more: WHY THE MOBILE MARKETING FUNNEL IS A CRUCIAL CONCEPT
To get their hands on advertisers’ budgets, fraudsters need to do one of two things:
They either need to make the advertisers’ attribution tracking system believe that they delivered valuable traffic, so they can claim the compensation for it although another source was responsible for sending this traffic. This approach usually requires sophisticated technology on the fraudsters’ side and targets the click or the install stage.
Alternatively, fraudsters need to create or simulate traffic themselves at the lowest possible cost and sell it to advertisers at inflated prices. This approach does not necessarily require sophisticated technology. It aims at the impression, click, or install stage.
Learn more: WHY YOU NEED ATTRIBUTION TRACKING FOR YOUR MOBILE APP
10 TYPES OF MOBILE AD FRAUD
As the mobile industry evolved, fraud evolved as well. Criminals develop new forms of fraud constantly and outdated strategies become obsolete. The following paragraphs will summarize the most common fraud types of the present:
- Ad Stacking
- Background Traffic
- Click Spamming
- Click Injection
- Click Bots
- Simple Install Bots
- Smart Bots
- Device Farms
- SDK Spoofing
- Compliance Fraud
Ad Stacking
The purpose of Ad Stacking is to charge multiple publishers for the same ad placement. This type of fraud can target either the impression stage or the click stage of the Mobile Marketing Funnel.
The fraudster stacks multiple ads of different publishers on top of each other in the same ad placement on their apps or websites. Only the ad on top is visible to the user. But at the moment he sees it, impressions for all of the stacked ads are counted. And all of the advertisers are charged, given that they run CPM campaigns.
To exploit CPC campaigns, the fraudster can use a modification of the Ad Stacking scheme where one click on the ad stack results in click reports for all of the stacked ads.
You can uncover ad stacking by identifying very low click rates (or very low click-to-install-conversion rates for CPC campaigns).
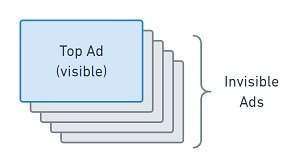
A Stack of Ads
Background Traffic
Another way to attack CPM campaigns is Background Traffic that is generated by malicious apps. This type of fraud aims to charge advertisers for ad impressions that the user does not see at all.
When a user minimizes an app without closing it, it keeps running in the background. The owner of a fraudulent app can exploit this behavior by “showing” ads that are not visible to the user.
Alternatively, the fraudster can run a program that automatically clicks the background ads without any action by the user. With this modification, Background Traffic can target CPC campaigns as well.
Just like ad stacking, background traffic schemes result in low click rates or low click-to-install-conversion rates.
Click Spamming
Click Spamming (also known as Click Flooding) attacks advertisers at the install stage. Fraudsters developed this method to pocket CPI compensations for real users who actually discovered the promoted app organically.
The basis for Click Spam is a malicious app that is controlled by the fraudster. This app creates enormous amounts of clicks on tracking links either while the user interacts with it or while it is running in the background. In any case, they happen without the user noticing them. If the user actually installs one of the promoted apps, the fraudster receives the CPI compensation as he has delivered the last click.
Click Spamming depends on luck because fraudsters cannot predict reliably whether a user with an infected device actually will install a targeted app. Thus, click spammers typically target popular apps with big user bases and significant organic traffic. By collecting and combining the tracking links of user acquisition campaigns for multiple different apps, they increase their chances of successfully stealing installs.
Detecting Click Spam is rather easy. As the fraudster needs to create exceptional high numbers of clicks, the click-to-install conversion rates for compromised publishers will be extremely low in comparison to legitimate traffic sources.
Click Injection
With Click Injection (also called Click Highjacking), fraudsters attack advertisers at the install stage by stealing the attribution of organic users. But unlike Click Spamming, this approach is more targeted and relies on sophisticated technology rather than on luck.
A fraudulent app that carries malware spies on the user’s device. More specifically, it spots new apps that the user is about to download. As soon as a download starts, the malware checks whether the fraudster’s system knows a tracking link for a UA campaign for this app. If it does, the malicious app fakes a click on this tracking link and tries to send it to the advertisers’ tracking system. When the user opens his new app, the tracking system attributes him to the fake click as it was the last click before the install. So in the end, the fraudster will receive the CPI compensation for an organic install.
Click Injection is a dangerous thread. Organic users tend to be high-quality users. Thus, traffic that consists of stolen organic users will be of high quality, too. You can spot indicators of Click Injection though: As the infected device sends the click report after the download process started, the time to install (TTI) will be very low.
Click Bots
Click bots simulate clicks on ad placements on apps and websites as well. But unlike Background Traffic, click bots do not run on the devices of real users. Instead, they run on emulators. These are programs that simulate a mobile device but actually run on a server that the fraudster controls.
The result of bot traffic is a very low click-to-install conversion rate. By comparing these rates by publishers, you will be able to identify traffic sources that use click bots.
Simple Install Bots
Just like click bots, install bots run on fraudsters’ servers, but they simulate app installs in addition to clicks.
Simple bots follow the user journey to the install stage. They create ad clicks and installs, but then they stop. As soon as the install is completed, they reset the (faked) device ID to pretend they are a new user and repeat the process. By doing so, bots can generate a lot of fake installs within a very short period of time.
Some companies, usually based in Asia, offer burst campaigns to push your app into the top charts. In many cases, they use bot traffic to reach this goal. Apple and Google consider bot traffic a manipulation of their algorithms. So if you use these services, you might be punished and got your app rejected.
To spot install bots, check out engagement rates. If you see a lot of installs from single publishers but no post-install events, this is a clear indicator of bot traffic. Another way to detect install bots is to compare install numbers from your MMP with download numbers from the app stores. Especially bots that are used in burst campaigns only fake clicks on the download button, but they do not generate app opens. Thus, they create enormous volumes of downloads, but not installs.
Smart Bots
Lately, fraudsters have developed more sophisticated bots. Their primary goal still is to attack advertisers on the install stage, but they do not stop there. They can also exploit CPE campaigns.
The fraudster reverse-engineers real user behavior after the install and programs his bots to copy this behavior. As a result, the bots do not stop as soon as they created fake installs. Instead, they perform post-install events and in some cases even in-app purchases in a timely plausible matter. In addition, smart bots create only small portions of fake traffic per source to avoid detection.
Finding smart bots by manual analysis of user data is almost impossible. The key is to identify traffic sources that deliver significant portions of users that show patterns of identical behavior. Unfortunately, this is very hard without sophisticated anti-fraud technologies based on Big Data.
Device Farms
Device farms or click farms are big operations that combine hundreds of real mobile devices and use them to create impressions and perform ad clicks, app installs, and post-install events on a mass scale. Sometimes, they are also used to write app store reviews or engage with social media profiles.
Device farms are either used by human operators who manually do clicks and installs, or they are remote-controlled by a computer that performs the desired actions. Usually, the IDs of the devices are reset after each walk-through, so they appear to be new devices to the advertiser’s MMP.
As fraudsters can copy real human behavior with device farms, it is not easy to detect them. A good approach is to look out for large portions of traffic that come from the same IPs or from the same device models and brands. Especially, if many outdated devices show up in tracking data, you should be suspicious and have a closer look at it.

Device Farm in China (Image Credits: PPC Protect)
SDK Spoofing
A relatively new and sophisticated type of fraud is SDK Spoofing or SDK Mimicking. It is a method that aims primarily at the install stage, although it can also attack the click or the engagement stage of the Mobile Marketing Funnel.
To prepare SDK Spoofing, the fraudster develops an SDK. This SDK seems to have a real value for app developers on the surface, but its real purpose is malicious. The fraudster then tries to make genuine developers add this SDK into their apps. Alternatively, he builds a simple app like a battery saver app or a flashlight on his own and implements the malicious SDK into it.
If people use the infected app, the SDK will record the communication of the app with MMPs. The fraudster will then analyze and replicate this communication to send fake install reports that make the MMPs’ servers think that real installs take place. In some cases, the fraudster even fakes post-install events to make his traffic look legitimate and hide his criminal actions even better. In the end, the fraudster will receive CPI compensations for installs that never happened.
SDK Spoofing is hard to detect because the fraudster uses real devices and also real app data to fake installs. You can find hints though: Each install report comes with information about the tracking SDK such as the SDK version number. Legitimate traffic includes the ID of the SDK version that is actually implemented into your app. But fake traffic might contain a wrong version number because the fraudster has faked it.
Compliance Fraud
Compliance fraud is one of the most versatile types of ad fraud because it can occur in many different shapes. It usually targets the install stage of the Mobile Marketing Funnel. But as it affects all stages of the funnel, it can also be used to attack advertisers that run CPM, CPC, or CPE campaigns.
A fraudster who performs compliance fraud disregards the targeting parameters that an advertiser has defined. By doing so, the fraudster can buy or generate traffic that is much cheaper than the traffic that the advertiser wants to have. Nevertheless, he sells it for premium prices and earns great margins.
Common ways to perform compliance frauds are:
- Rebrokering a campaign although the advertiser wants direct traffic only. By buying cheap low-quality traffic from 3rd parties, the fraudster can reduce the work and costs on his side and make it harder for the advertiser to identify the original source.
- Delivering incentivized traffic although the advertiser pays for non-incentivized traffic. Incentivized traffic is up to 80% cheaper but usually has a much lower quality.
- Sending traffic from countries with low prices and low user LTVs (for instance India) when the advertiser expects installs from regions with high prices and high LTVs (such as the United States).
- Using creatives that were not approved by the advertiser and that trick the user into interacting with them by making false claims about the app.
In theory, identifying compliance fraud is relatively easy, given your MMP provides the necessary data. You must be able to compare traffic sources by publisher and sub-publisher. With data about the country where traffic comes from, but also about device languages, you can find traffic providers that do fraudulent geo-targeting. And by using install and event data to calculate engagement rates, you can identify users of very low quality who might be a sign of incentivized traffic.
Combinations of Multiple Fraud Types
In some cases, fraudsters combine two or more fraud tactics to do the biggest possible damage. For instance, it is common to use Ad Stacking to create enormous amounts of clicks that are needed for successful Click Spamming.
10 TIPS TO PROTECT YOUR APP AGAINST MOBILE AD FRAUD
To protect yourself against all types of fraud is hard to do. Since fraudsters constantly develop new methods, it makes sense to look out for a reliable anti-fraud partner once your marketing budgets grow to significant levels.
Nevertheless, you can take some measures yourself. Here are 10 tips to protect yourself against ad fraud:
- Do not use tracking tools that utilize Open Source SDKs. They are much more prone to reverse engineering and thus to fraud than the SDKs of MMPs that focus on security.
- Demand transparency from your user acquisition partners. If ad networks disclose the names of their publishers instead of masking them with anonymous IDs, fraudsters will have it much harder to sneak their traffic into the funnel.
- In any case, insist on receiving publisher IDs (or names) via tracking links, so you are able to analyze traffic based on single sources.
- Make sure that the insertion order that you sign with your UA partners includes precise targeting parameters (OS, country, demographics) as well as limitations. State clearly whether you accept incentivized traffic and rebrokering or not. Consider excluding outdated device models or OS versions.
- Provide a list of benchmarks to your UA partners and tell them to use it as a reference when optimizing traffic. These are useful metrics for this purpose:
- the average click-through rate
- the average click-to-install conversion rates
- average event conversion rates
- the average time to install
- Set daily budget caps for your campaigns. If possible, also set daily caps on a publisher level to avoid losing too much money to fraudulent sources in the short term.
- When checking for suspicious traffic, focus at the stage of the Mobile Marketing Funnel where the payment happens: If you buy CPM traffic, look out for impression fraud, but If you pay per install, check for install fraud.
- Compare data from your tracking provider to data from other sources. Many fraud types will create unreasonable discrepancies. For example, if your MMP shows a lot of in-app events, but session time is going down according to your analytics tool, the events might be fake. Another useful analysis is the comparison of installs from your tracking tool and downloads from App Store Connect or the Google Play Developer Console. If they differ significantly, the traffic might be illegitimate.
- Create a blacklist of publishers (or publisher IDs) that deliver fraud or low-quality traffic. Update this list as you optimize campaigns, and give it to UA partners whenever you start a new campaign.
- Finally, do not hesitate to ask for refunds for fraudulent traffic. It is the ad network’s job to deliver legitimate users. If they fail to do so, you do not have to pay for the damage.
Conclusion
Ad fraud is a thread to every advertiser in the mobile ad industry. Especially when you buy traffic from intermediates like ad networks, affiliate networks, or agencies, you will face fraud at some point.
Here is an overview of the most common fraud types and how you can detect them:
| Fraud Type | Attacked Funnel Stage | Prequesition | Detection |
|---|---|---|---|
| Ad Stacking | Impression, Click | real Device, manipulated Ad Placement | low Click Rate, low Conversion Rate |
| Background Ads | Impression, Click | real Device, malicious App | low Click Rate, low Conversion Rate |
| Click Spamming | Click | real Device, malicious App | low Conversion Rate |
| Click Injection | Install | real Device, malicious App | low Time to Install |
| Click Bots | Click | emulated Device | many Clicks & no Installs |
| Simple Install Bots | Install | emulated Device | many Download & no Installs, no Post-Install Events |
| Smart Bots | Install, Engagement | emulated Device, User Behavior Data | Patterns of Identical Behavior |
| Device Farms | Impression, Click, Install, Engagement | real Devices | same (outdated) Device Models, same location |
| SDK Spoofing | Install | emulated Device, real Device Data | wrong Tracking SDK Version Number |
| Compliance Fraud | Impression, Click, Install, Engagement | real Devices | wrong Country, wrong IPs, low Conversion Rate |
If you have only small marketing budgets and want to make sure to not become a victim of fraudsters, focus on channels that do not use 3rd party traffic, for example, Apple Search Ads or Facebook Ads.
Learn more: BEST PRACTICES FOR APPLE SEARCH ADS – A GUIDE FOR BEGINNERS
